Encryption
Tokopedia apply encryption for information related to buyer information.
Introduction
According to Tokopedia policy to protect Tokopedia user from unwanted party, we would like to increase our security system throught encryption method. Current information that labeled as sensitive information are buyer's email, address detail, and phone number. Providing this sensitive information outside Tokopedia platform is not a good approach. In this case, we would like to make sure that the right party is eligible to access these data.
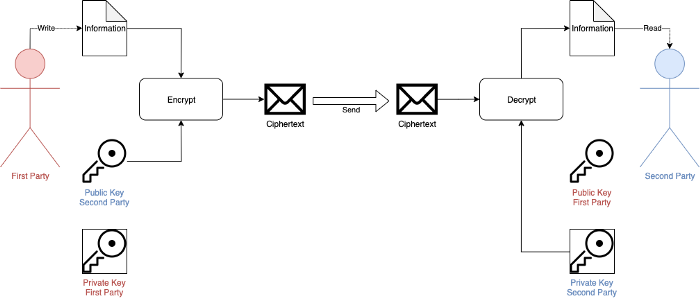
The encryption method that we want to implement in SellerAPI system using asymmetric key encryption named RSA encryption. The implementation shows that the First Party (Tokopedia Seller API) will encrypt the data using Second Party's Public Key. Second Party (Partner/Enabler) should decrypt the encrypted message using their own Private Key. When encrypted, the message always unique eventhough the data is the same.
This method should be implemented by Partner on endpoint module Order (Get Single Order, Get All Order, Order Notification Webhook). Regarding the implementation strategy we will provide new endpoint for testing API, webhook retry for testing, and switcher for current endpoint and webhook. You can check more details in the next section.
Timeline
Partner should implement RSA Encryption within the timeline below. Regarding any concern about this timeline please contact us from ticketing system.
September 28th, 2020
Partner can start to Register their Public Key. Please follow the tutorial for registering their Public Key here
November 30th, 2020
All Partner should have implement and switch all the endpoint
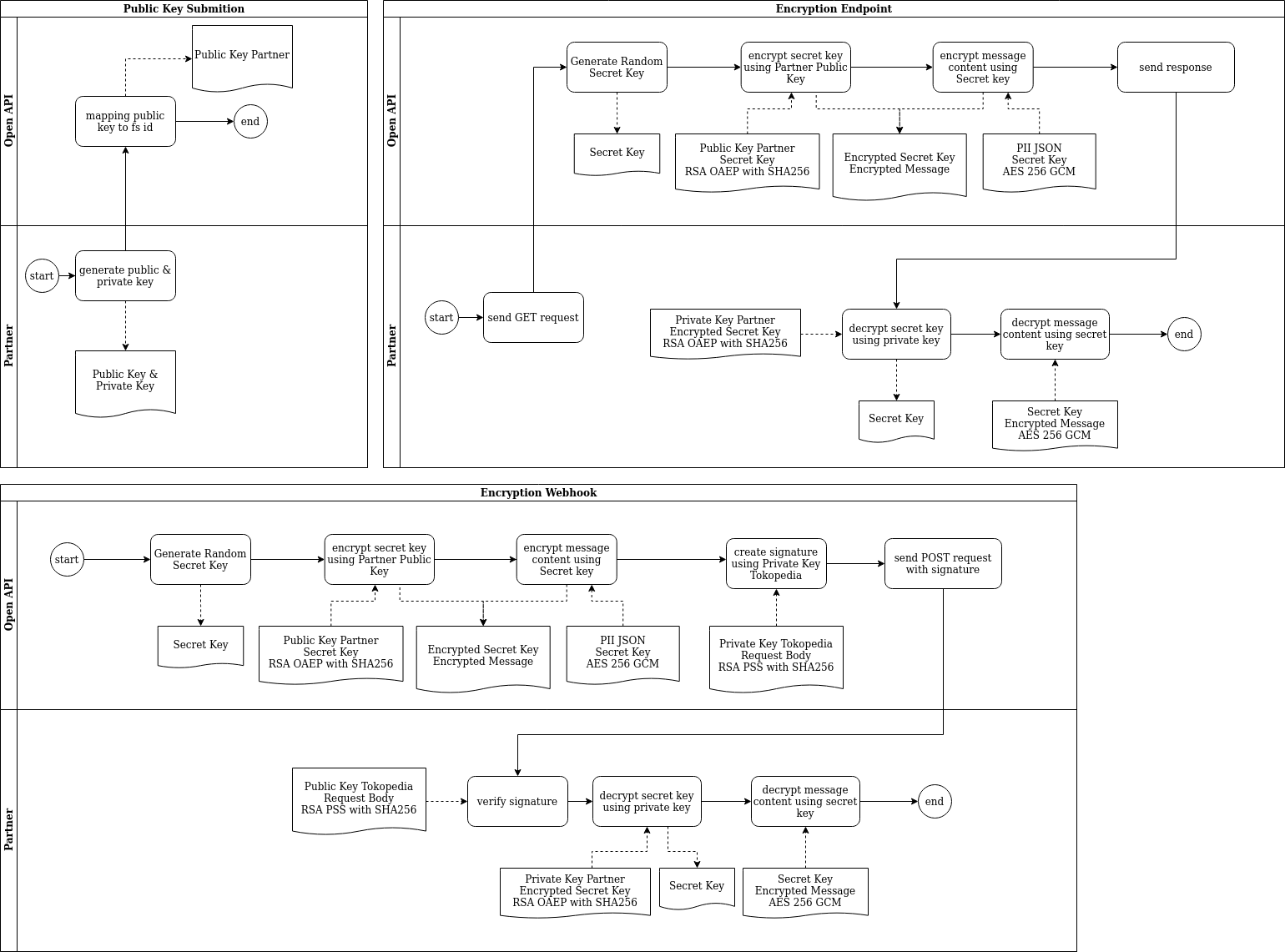
Flow Chart
There are three type of flow for encryption process: Register Public Key, Encryption Endpoint, and Encryption Webhook.
Impacted Features
Getting Started
Toolkit
If you want to try the algorithm without using your production environment you can download testcase zip file. ZIP contains files below:
before.jsonfile contain get single order response before using encryptionresponse.jsonfile contain get single order response after using encryption, where the value ofcontentandsecretcan be use testcase material.test.public.txtfile public key that was use to generatecontentand secret from previous file.expected.jsonfile contain json result of decryption process.test.private.txtfile private key that can be use to decryptsecret.check.txtfile contain information validation from this testcase. Information include here such as secret key, nonce as base64, and cipher text as base64.decrypt.gofile contain example code to decrypt message using Golang.
You can download all the script for entire encryption process here.